Embark on a journey through the realm of cybersecurity best practices, where the protection of your digital assets takes center stage. As we delve into the importance, key elements, implementation strategies, and emerging trends, you'll gain valuable insights to fortify your defenses in today's cyber landscape.
Importance of Cybersecurity Best Practices
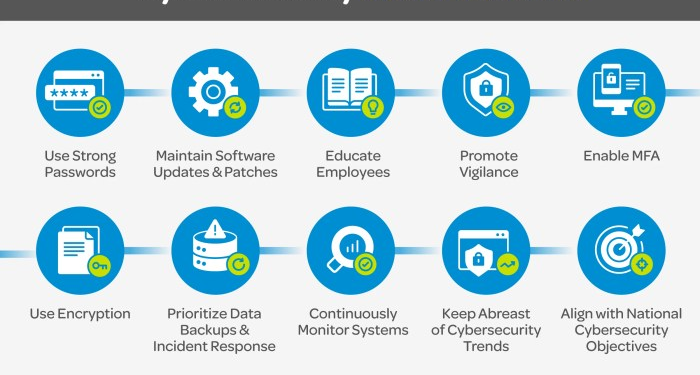
In today's digital landscape, cybersecurity best practices are crucial to protect sensitive information and prevent cyber attacks. By following these practices, individuals and organizations can minimize the risks associated with cyber threats.
Risks of Not Following Cybersecurity Best Practices
- Exposure to Data Breaches: Without proper security measures in place, hackers can easily gain access to confidential data, leading to potential data breaches.
- Identity Theft: Lack of cybersecurity best practices can result in identity theft, where personal information is stolen and misused.
- Ransomware Attacks: Failure to implement cybersecurity measures can make systems vulnerable to ransomware attacks, where malicious software encrypts files and demands payment for decryption.
Benefits of Cybersecurity Best Practices
- Protection of Sensitive Information: Following cybersecurity best practices helps in safeguarding sensitive data such as financial records, personal information, and intellectual property.
- Prevention of Cyber Attacks: Implementing strong security protocols can help prevent cyber attacks like phishing, malware infections, and denial-of-service attacks.
- Maintaining Trust: By prioritizing cybersecurity best practices, organizations can build trust with customers, partners, and stakeholders, demonstrating a commitment to data protection.
Key Elements of Cybersecurity Best Practices

In today's digital age, having a robust cybersecurity strategy is essential to protect sensitive data and prevent cyber attacks. There are several key elements that form the foundation of effective cybersecurity practices.
Role of Encryption
Encryption plays a crucial role in cybersecurity by converting data into a secure format that can only be accessed with the right decryption key. This helps in safeguarding information from unauthorized access and ensures data confidentiality.
Access Controls
Implementing access controls is vital in limiting the individuals who can access sensitive data within an organization. By setting up user permissions and authentication mechanisms, organizations can prevent unauthorized users from gaining access to critical information.
Regular Software Updates
Regularly updating software is essential to patch security vulnerabilities and protect systems from potential cyber threats. Outdated software can be exploited by hackers to gain unauthorized access, making timely updates a crucial aspect of cybersecurity best practices.
Employee Training and Awareness Programs
Employee training and awareness programs are key to maintaining cybersecurity hygiene within an organization. By educating employees about potential threats, safe practices, and the importance of data security, organizations can empower their workforce to be the first line of defense against cyber attacks.
Implementing Cybersecurity Best Practices
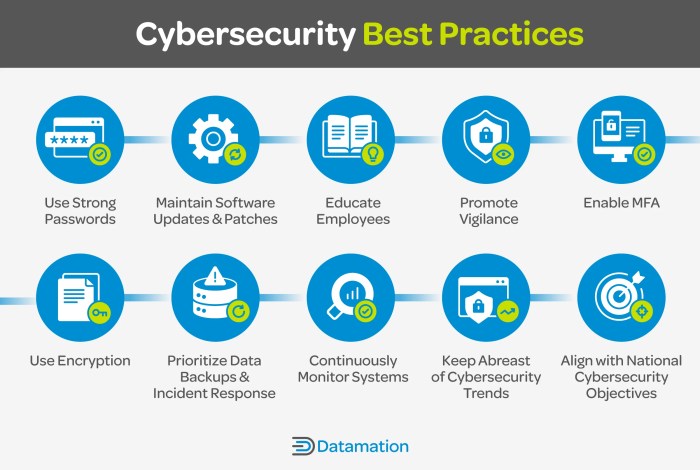
Implementing cybersecurity best practices is essential for organizations to protect their sensitive data and systems from potential cyber threats. By following a structured approach, companies can enhance their overall security posture and minimize the risk of cyber attacks.
Steps for Organizations to Implement Cybersecurity Best Practices Effectively
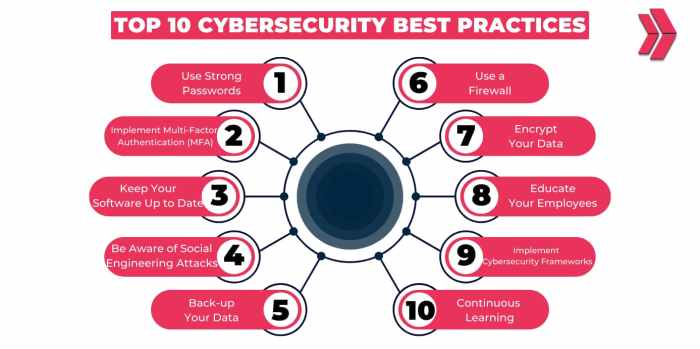
- Educate employees on cybersecurity awareness and best practices to foster a culture of security within the organization.
- Implement multi-factor authentication (MFA) to add an extra layer of protection for user accounts and systems.
- Regularly update software and systems to patch known vulnerabilities and reduce the risk of exploitation by cyber criminals.
- Utilize encryption to protect sensitive data both at rest and in transit, ensuring confidentiality and integrity.
Conducting Regular Security Audits and Risk Assessments
Regular security audits and risk assessments are crucial for identifying vulnerabilities and weaknesses in an organization's security infrastructure. By conducting these assessments, organizations can proactively address potential threats and enhance their overall security posture.
Significance of Creating Incident Response Plans and Backup Strategies
- Developing incident response plans enables organizations to respond effectively to security incidents and minimize the impact on operations.
- Implementing backup strategies ensures that critical data is regularly backed up and can be restored in the event of a ransomware attack or data breach.
- Regularly test incident response plans and backup strategies to ensure they are effective and up to date.
Emerging Trends in Cybersecurity Best Practices
As technology continues to advance, new trends in cybersecurity best practices have emerged to address evolving threats and technologies. Organizations must stay informed and adapt to these trends to enhance their cybersecurity posture.
Zero-Trust Security Models
Zero-trust security models have gained popularity due to their proactive approach to cybersecurity. This model operates on the principle of "never trust, always verify," requiring continuous authentication and authorization for all users and devices attempting to access the network.
AI-Driven Cybersecurity Solutions
Artificial Intelligence (AI) is revolutionizing cybersecurity by enabling proactive threat detection and response. AI-driven cybersecurity solutions can analyze vast amounts of data in real-time to identify anomalies and potential security breaches, enhancing overall security measures.
Impact of Remote Work and Cloud Computing
The shift to remote work and increased reliance on cloud computing has significantly impacted cybersecurity best practices. Organizations now face new challenges in securing remote endpoints and data stored in the cloud, requiring robust security measures to mitigate risks.
Adapting to Evolving Threats and Technologies
Organizations must continuously adapt to evolving threats and technologies to stay ahead of cybercriminals. This includes implementing multi-layered security measures, conducting regular security assessments, and providing ongoing cybersecurity training for employees to ensure a strong defense against cyber threats.
Closing Notes
In a world where cyber threats lurk at every corner, embracing cybersecurity best practices is not just a choice but a necessity. By staying informed, implementing robust strategies, and adapting to evolving trends, you equip yourself with the tools needed to safeguard your valuable data and navigate the digital realm securely.
Q&A
How often should software updates be performed?
Regular software updates should be conducted promptly after release to patch vulnerabilities and enhance security measures.
Why is employee training essential for cybersecurity?
Employee training is crucial to raise awareness about potential threats and ensure adherence to security protocols, reducing the risk of cyber incidents.
What are incident response plans?
Incident response plans Artikel steps to be taken in case of a cybersecurity breach, facilitating a swift and organized response to mitigate damages.